Invisible fabrication of secret shares of signature images at the user end
4.6 (592) In stock

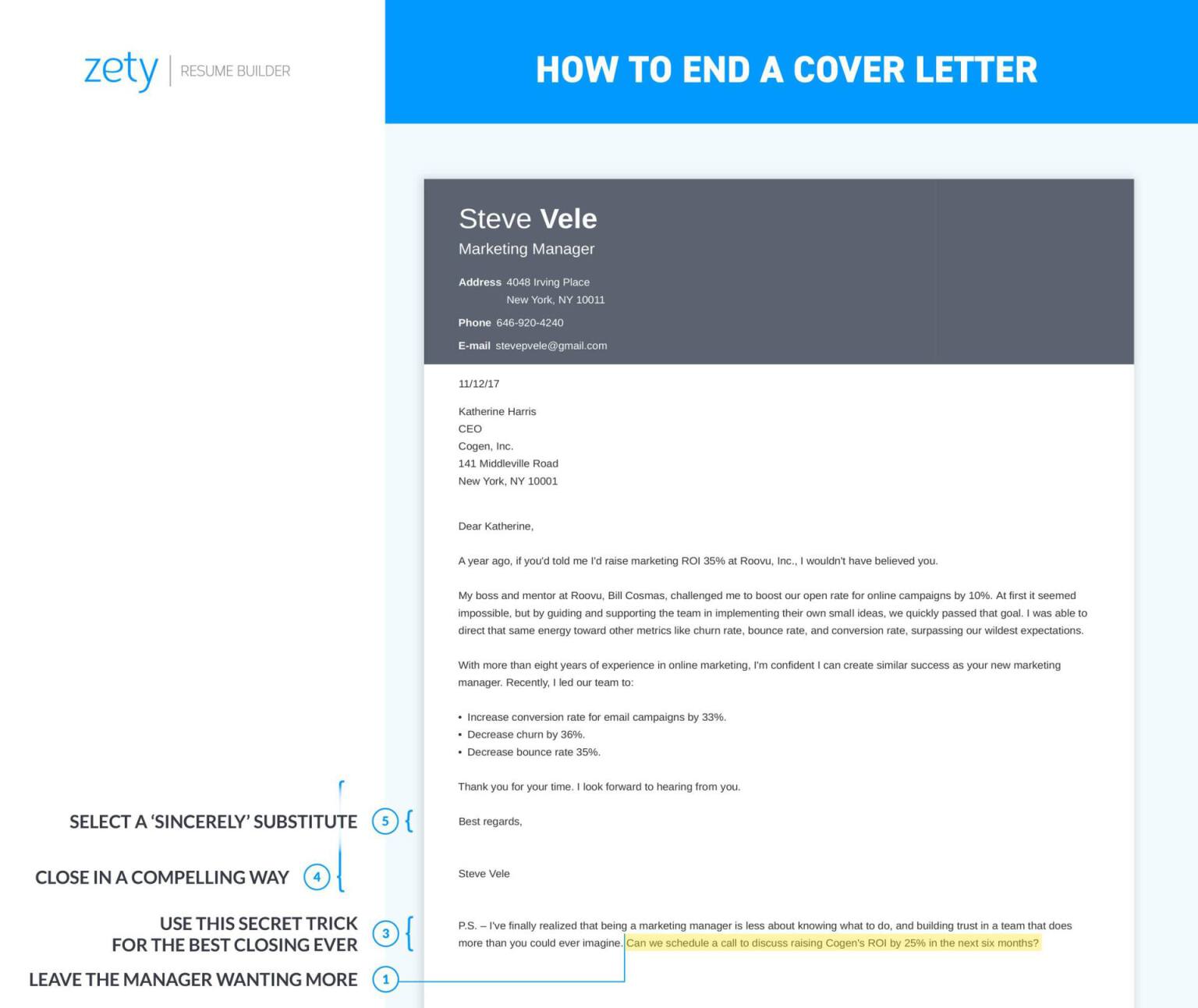
How to End a Cover Letter? Closing Examples & Tips

Telegram Channels Unveiled: The Hidden Dangers Lurking in Shared Files - SOCRadar® Cyber Intelligence Inc.

A reversible and lossless secret image sharing scheme with authentication for color images - ScienceDirect

Hiding Code Inside Images: How Malware Uses Steganography

How to Create Anonymous (Fake) Email to Protect Online Identity?

Secret painting, 1967-1968 by Art & Language

Dynamic Authentication Protocol Using Multiple Signatures

Avoiding Security Missteps with OAuth 2.0 Implementations
Cryptography - Wikipedia
Make Transparent Signature from Picture
PDF Signature Benefits, Ascertia
How to create transparent .png signature in GIMP. Easier than
 Women Long Dress V Neck Maxi Dresses Ladies Kaftan Holiday Plus
Women Long Dress V Neck Maxi Dresses Ladies Kaftan Holiday Plus Girls Clothes Size 6t Pants Solid Warm Winter Toddler Girl Suspender Overalls Girls Pants Cute Dance Clothes for Kids (Brown, 6-12 Months) : Clothing, Shoes & Jewelry
Girls Clothes Size 6t Pants Solid Warm Winter Toddler Girl Suspender Overalls Girls Pants Cute Dance Clothes for Kids (Brown, 6-12 Months) : Clothing, Shoes & Jewelry Olga Secret Hug Bikini Sissy Panty Delicate LACE 9/2XL PINK Rose 0913J3
Olga Secret Hug Bikini Sissy Panty Delicate LACE 9/2XL PINK Rose 0913J3 Cape Town Travel Guide Marriott Bonvoy Traveler
Cape Town Travel Guide Marriott Bonvoy Traveler JOCKEY Women Shapewear - Buy JOCKEY Women Shapewear Online at Best Prices in India
JOCKEY Women Shapewear - Buy JOCKEY Women Shapewear Online at Best Prices in India LASCANA Push-up Bra in Cream
LASCANA Push-up Bra in Cream