Layer 8 Hacking - Linking the OSI Model with the NIST Triangle
4.8 (161) In stock

Layer 8 Hacking can be defined as hacking above and beyond the technical layers; hacking by targeting the user, the business processes, or the organization i

PDF) Modelling computer networks for further security research
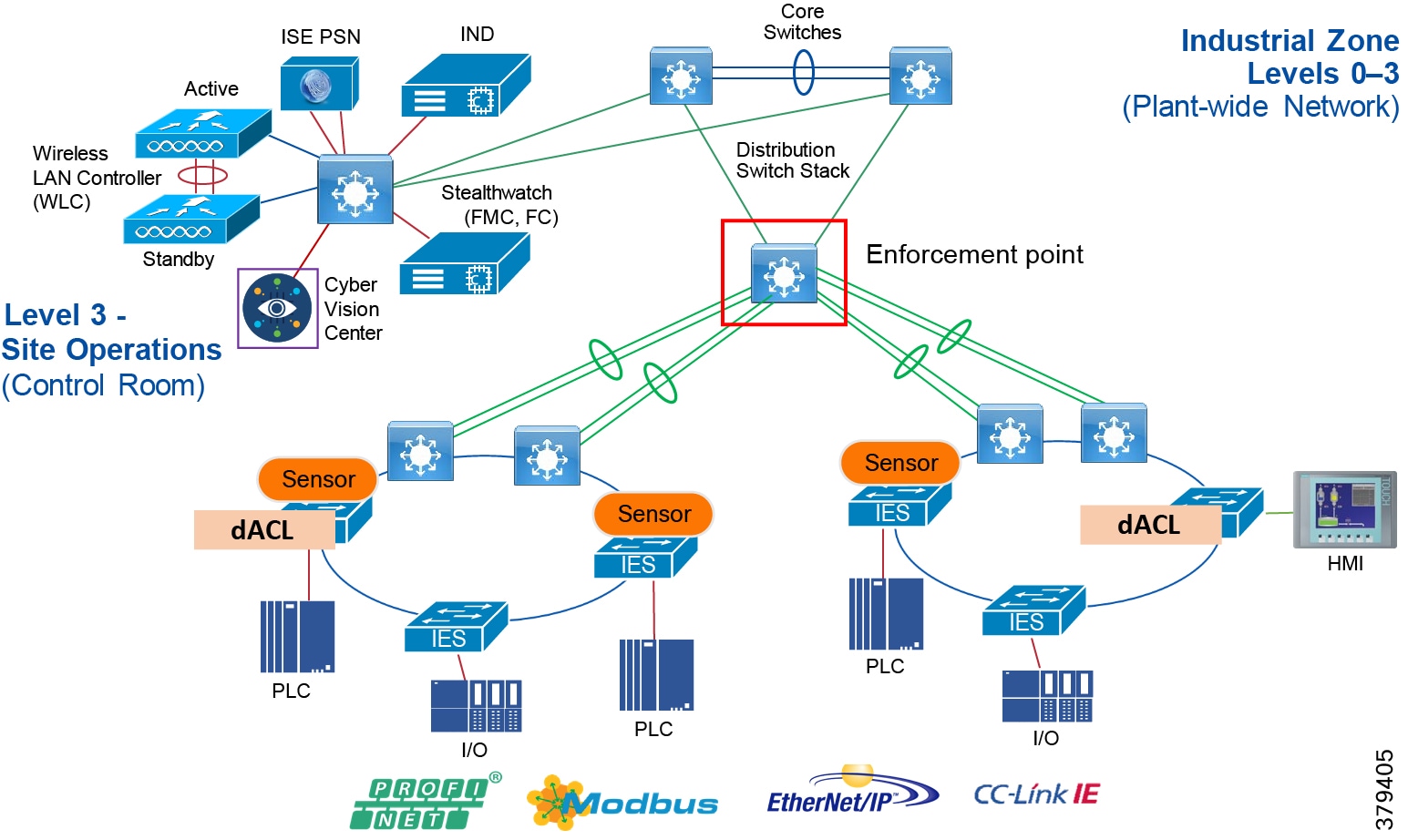
Networking and Security in Industrial Automation Environments
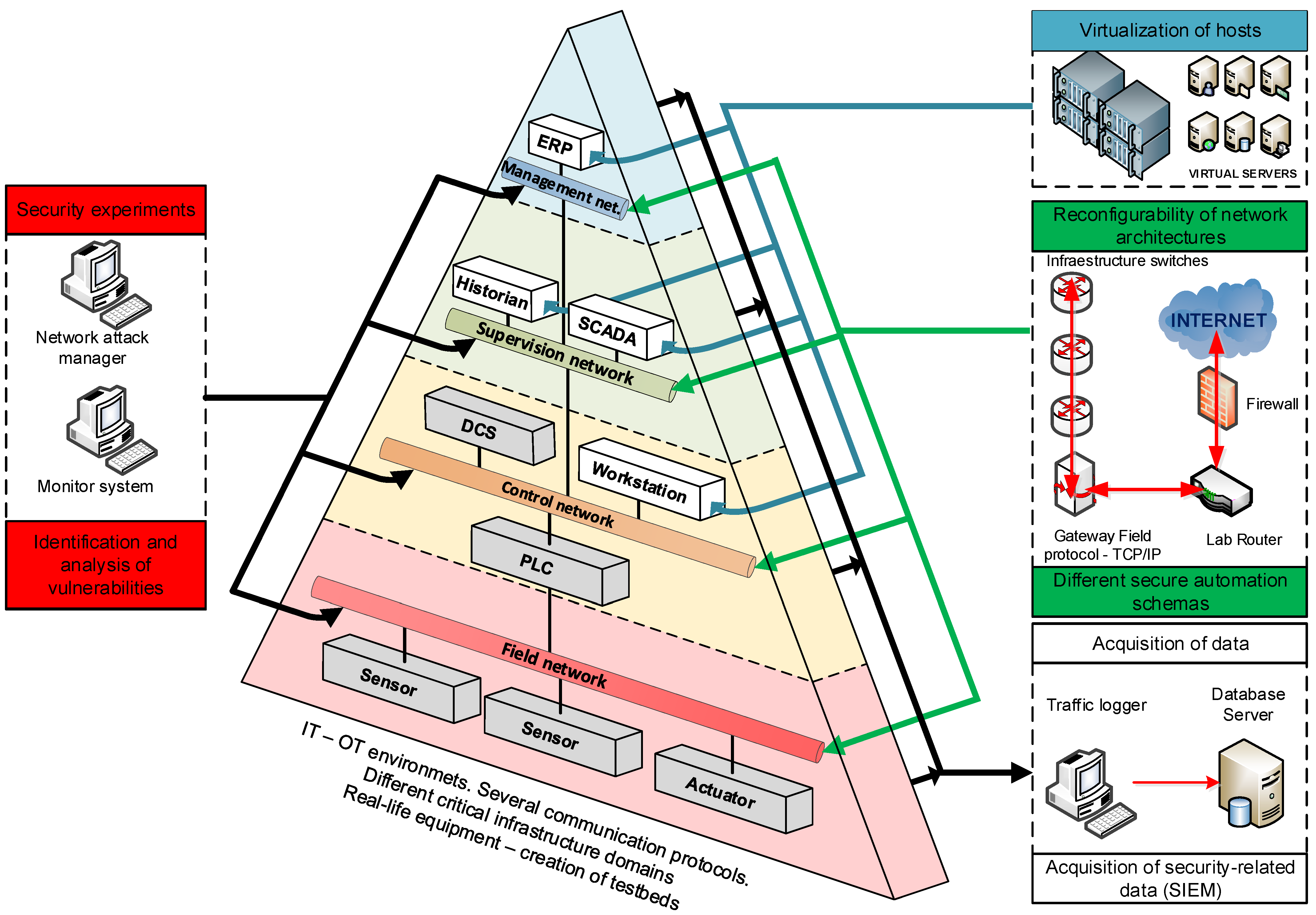
Applied Sciences, Free Full-Text
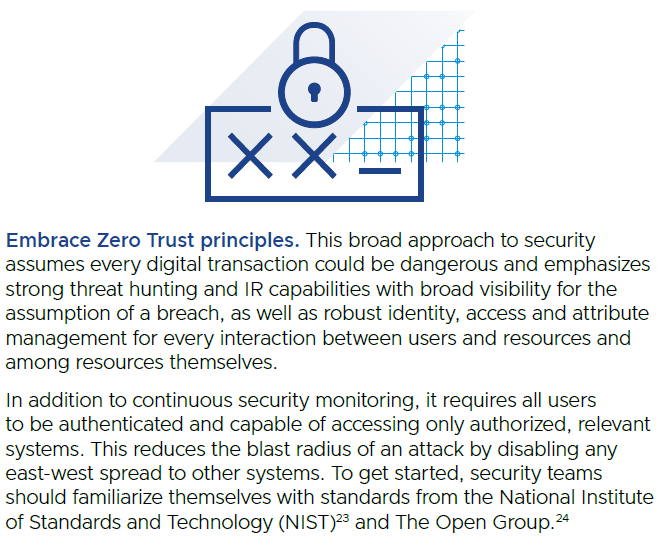
How VMware can Secure Mobile Endpoints with Threat Defense (MTD
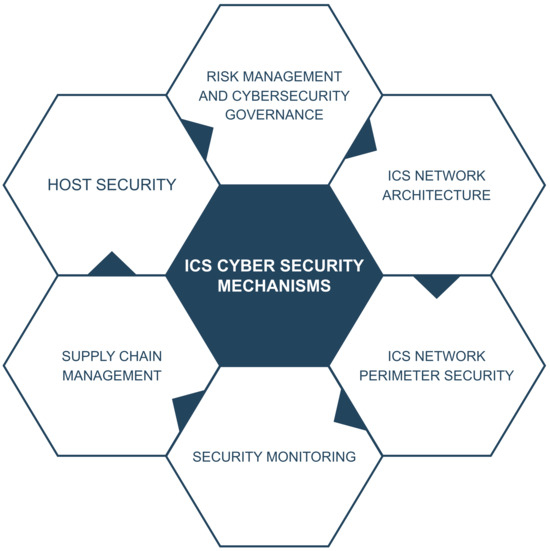
Sensors, Free Full-Text

Seven Layers of OSI Model in an easy way

A survey of cyber security threats and solutions for UAV

Sensors, Free Full-Text

Security Threats at OSI layers
Layers and Models

Securing Layer 8 – Open Sourcerers

Cyber Terrain”: A Model for Increased Understanding of Cyber Activity
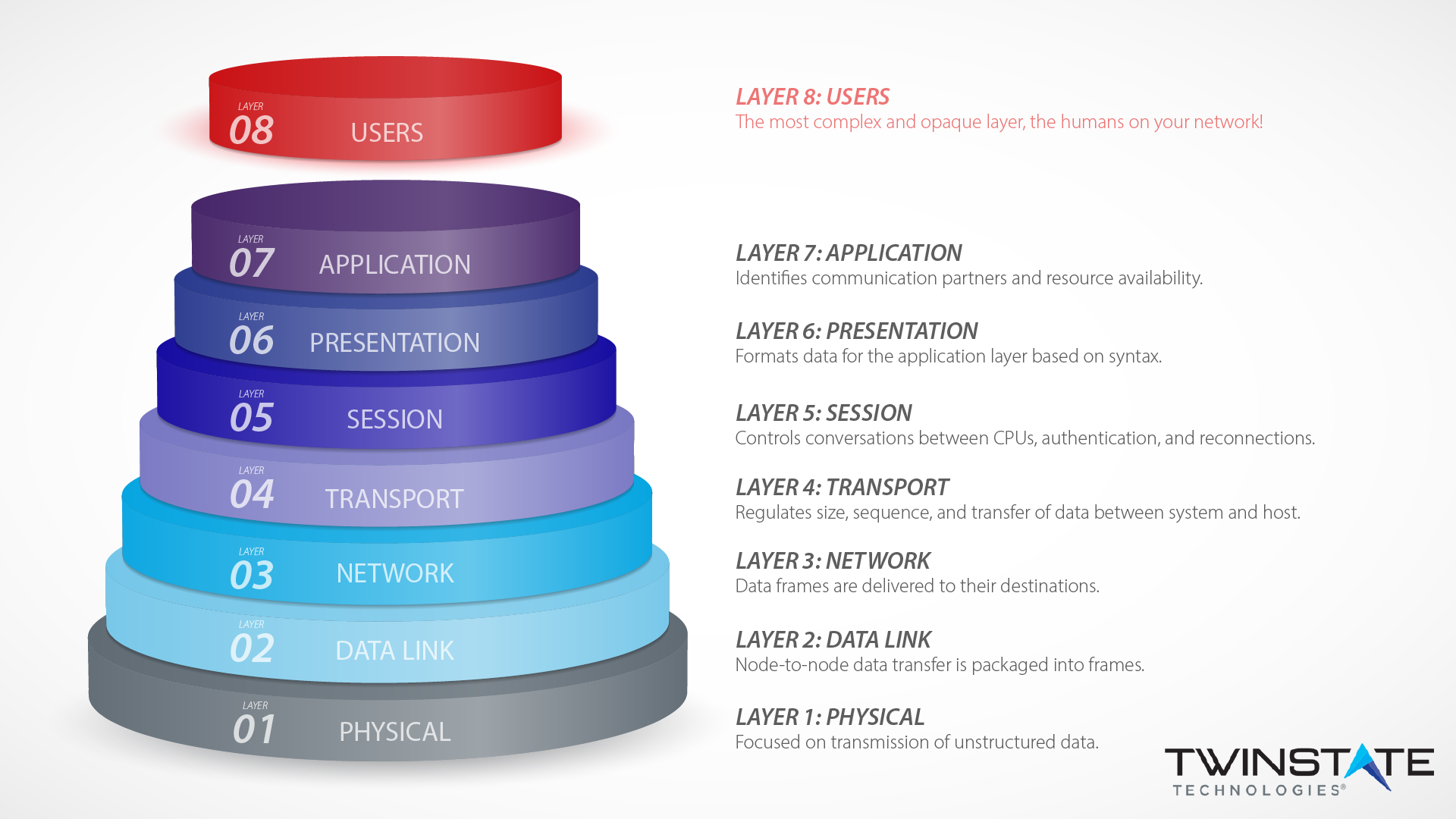
Layer 8 Technology: How We Protect Users at our Plattsburgh Office
Specialist for Layer 8 Problems T-Shirt - 24h delivery
What is an 8-Layer PCB Stackup? - PCB Directory
Layer 8 Men's Boxer Brief for sale
 SAYFUT Postpartum Belly Band Postpartum Recovery Belt Wrap Cotton
SAYFUT Postpartum Belly Band Postpartum Recovery Belt Wrap Cotton Porsche and Spark bring out the Mission E in 1:18
Porsche and Spark bring out the Mission E in 1:18 I'm a Lidl expert - my fun aisle finds under $10 to get you set for summer
I'm a Lidl expert - my fun aisle finds under $10 to get you set for summer NVGTN Flourish Seamless Bra - Aqua
NVGTN Flourish Seamless Bra - Aqua Tonus Elast Post Mastectomy Lymphedema Compression Arm Sleeve 23-32 mmHg - 0403 - Ultimate Encounter
Tonus Elast Post Mastectomy Lymphedema Compression Arm Sleeve 23-32 mmHg - 0403 - Ultimate Encounter Herringbone Pinstripes Leggings, The 365 Edition
Herringbone Pinstripes Leggings, The 365 Edition