Attackers can force Echos to hack themselves with self
5 (734) In stock

Popular “smart” device follows commands issued by its own speaker. What could go wrong?

What Is Alexa (and What's the Best Alexa Speaker for 2024

Sensors, Free Full-Text

Practical Social Engineering: A Primer for the Ethical Hacker

Internet of things' security introduction for EMS leaders

Hack Defense

Defcon 2018: Echo hack turned speaker into spy bug - Gearbrain

How to Protect Your Devices Against Meltdown, Spectre Bugs

Hacking reality
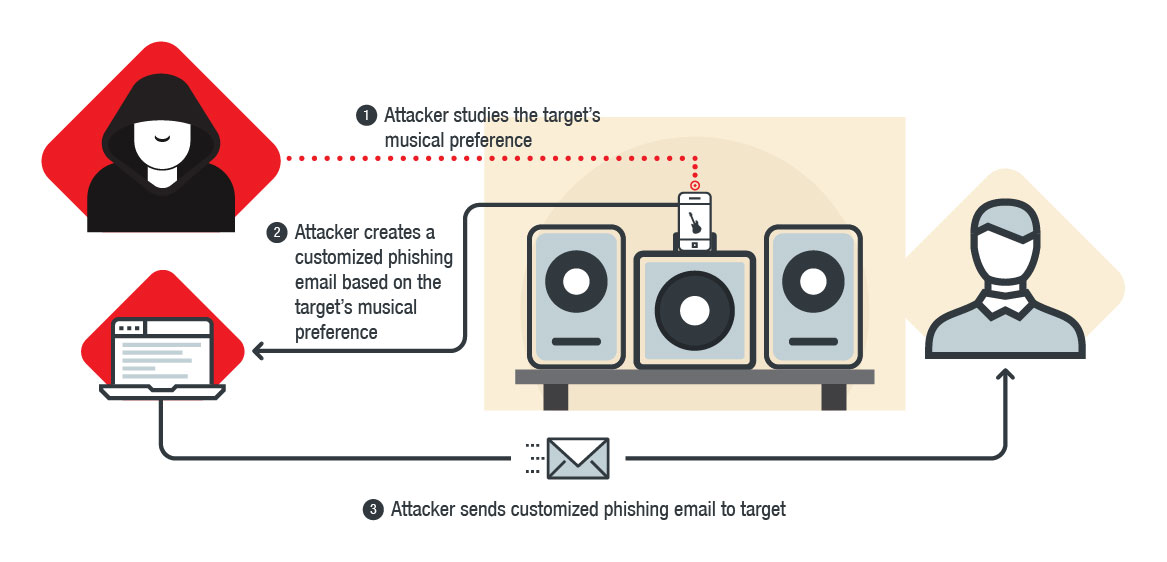
Hackers can remotely control thousands of Sonos and Bose speakers

Hack Defense

CVE-2023-49291 and More – A Potential Actions Nightmare – Adnan

What is a DDoS Attack and How Do DDoS Attacks Work?
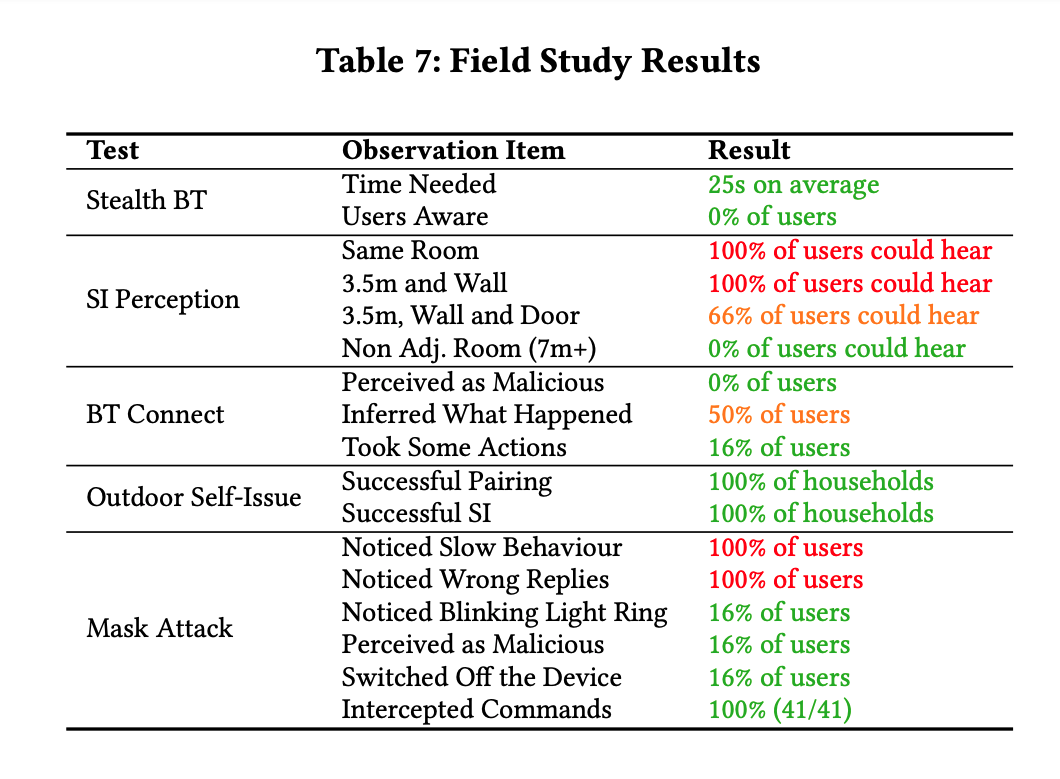
Attackers can force Echos to hack themselves with self
What is a Cyber Attack? Definition and Related FAQs

8 steps to being (almost) completely anonymous online
What is Alexa and what can Echo do?





