Attackers can force Echos to hack themselves with self-issued commands
5 (394) In stock

Popular “smart” device follows commands issued by its own speaker. What could go wrong?

Attackers can force Echos to hack themselves with self-issued commands
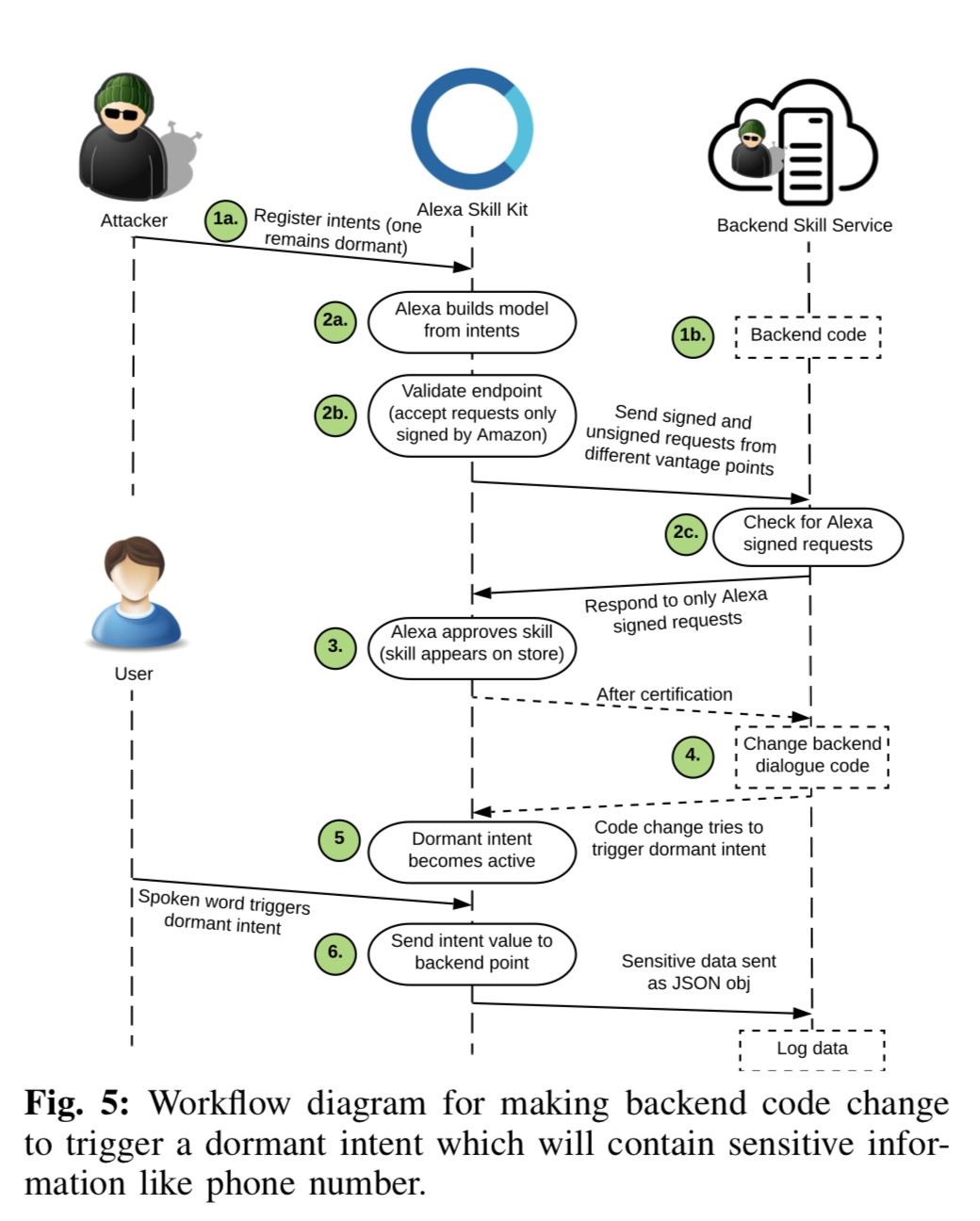
Mapping vulnerabilities in echo using alexa skills

API security, vulnerabilities and common attacks
Hacking ISPs with Point-to-Pwn Protocol over Ethernet (PPPoE) - TIB AV-Portal

Computer Systems Security: Planning for Success
What is a Cyber Attack? Definition and Related FAQs

Best Home Security Systems That Work with Alexa in 2024

JCP, Free Full-Text

Echos Hack Themselves, Fraud Is Flourishing on Zelle, Samsung Galaxy Source Code Stolen - Shared Security Podcast
Hack I.T.: Security Through Penetration Testing T. J. - HackBBS
GitHub - seeu-inspace/easyg: Here I gather all the resources about hacking that I find interesting

Hacking reality
Echo Dot (5th Gen 2022) - Smart Speaker with Clock and Alexa - Cloud Blue
Echo Dot with Clock (5th Gen, 2022)
What is Alexa and what can Echo do?
 2PCS Kids Girls Active wear Set Tank Crop Tops with Athletic Leggings Outfit
2PCS Kids Girls Active wear Set Tank Crop Tops with Athletic Leggings Outfit Skin Perfect Primer Facial Ruby Rose
Skin Perfect Primer Facial Ruby Rose Mens Adidas Tear Away Snap Track Pants Large - Gem
Mens Adidas Tear Away Snap Track Pants Large - Gem Public Notice for US-Brazil Projects: Frequently Asked Questions - U.S. Embassy & Consulates in Brazil
Public Notice for US-Brazil Projects: Frequently Asked Questions - U.S. Embassy & Consulates in Brazil Kendall Jenner's favourite activewear Gymshark launches new Flex collection in Australia
Kendall Jenner's favourite activewear Gymshark launches new Flex collection in Australia Wacoal Lace Strapless Bra - Farfetch
Wacoal Lace Strapless Bra - Farfetch